Applications are becoming increasingly complex and so are the threats they face. Modern, distributed systems need to connect to multiple data, leaving them exposed to more cyber-attacks and data breaches.
The diversity of this threat landscape and the speed at which attackers exploit weaknesses make traditional security practices largely ineffective. This is where observability comes in.
What is observability-driven development?
Observability-driven development (ODD) aims to design, build, and deploy highly visible systems by embedding observability into the entire software development lifecycle, down to the initial stages of instrumenting code. Unlike traditional monitoring, which focuses only on the application`s health, observability provides a holistic view of the system`s behavior through runtime data.
Embedding observability in development
Observability-driven development emerges as a way to observe, maintain, and optimize complex systems. By leveraging metrics, logs, traces, events, and observability tools, development teams can:
-
Understand the root causes of issues affecting the system. While monitoring tells you what is wrong, observability tells you why something is wrong.
-
Gain end-to-end visibility into the system, from the application layer down to the network layer.
-
Streamline the development process and daily operations through observability pipelines and automation.
-
Identify performance issues early on and resolve bottlenecks, including those coming from complex systems like microservices and cloud-native applications.
-
Reduce incidents and downtime, and continuously improve application performance and user experience.
For a more in-depth account of what observability is and how to implement it in the software development life cycle, check out our articles below:
The convergence between observability and security
As organizations expand across a mix of technologies, including cloud containers, microservices, low-code, and no-code tools, the attack surface also expands, leaving applications more vulnerable.
Modern systems are also becoming increasingly interdependent, making it harder to pinpoint the precise cause of an incident. This turns the kind of visibility created by observability into a prerequisite for any solid security strategy.
Understanding security observability
By leveraging the internal visibility provided by observability and combining it with security data, development teams can foster what`s known as security observability. Security observability allows IT Ops, DevOps, and security administrators to:
-
get a complete picture of the application`s security status
-
detect and investigate security incidents in real-time
-
resolve issues fast and minimize damage
-
secure the system against future, expected threats
Observability platforms add another layer of insight to traditional security monitoring. Unified observability solutions bring all data sources into one platform, creating a single source of truth for security teams. Advanced technologies such as AI, machine learning, and automation further help security teams to make sense of this consolidated data and avoid monitoring fatigue.
Benefits of integrating observability and security
Observability-driven security comes with several significant advantages over traditional security monitoring.
1. Understanding the root cause of security incidents
Observability tools allow teams to leverage AI and root cause analysis to understand and solve issues. Rather than sifting through thousands of similar logs trying to identify correlations, DevOps teams can use machine learning to identify and remedy the underlying factors that led to a security incident.
2. Faster response time to security breaches
Observability provides teams with the necessary context and data to act fast on security incidents. By monitoring events across the entire infrastructure in real-time, observability platforms allow security administrators to notice unusual activity early on and to quickly investigate and take action.
3. Ability to predict threats
As cyber threats are becoming more sophisticated, reactive measures are no longer enough. A proactive approach is required to stay ahead of attacks and secure applications against them before they take place. The predictive analysis enabled by observability tools, coupled with root cause analysis, can provide valuable insight into the most vulnerable areas of an application.
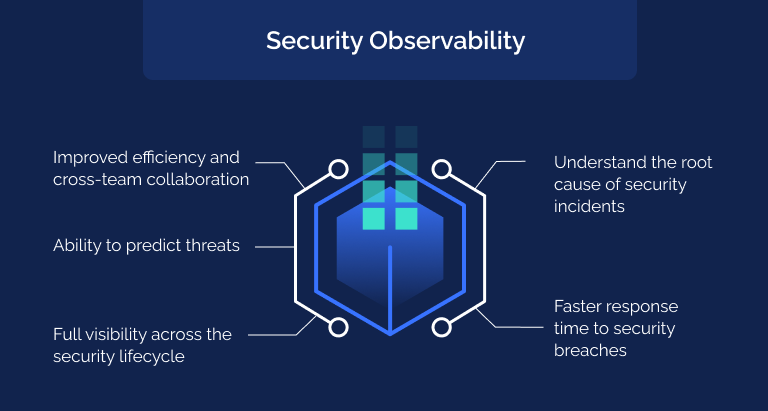
4. Full visibility across the security lifecycle
Traditional monitoring focuses on high-level metrics, which makes tracking issues across the system more difficult. Observability provides more granular insight into security incidents, enabling teams to track them step by step, from the very first moment a security incident was identified all the way to the moment it was resolved.
5. Improved efficiency and cross-team collaboration
Observability, and the ecosystem of tools it relies on, support teams in automating and simplifying a lot of their daily operations. Observability empowers teams to make better, more informed decisions and to cut down on the number of security alerts they have to filter through.
It also encourages cross-team collaboration and better coordination between developers, security engineers, and IT engineers to resolve incidents. IT teams involved in observability collect huge amounts of data which they can share with security teams, eliminating duplicate work and data silos.
Unlocking the power of observability in building secure applications
Securing applications against attacks is not just a matter of implementing cybersecurity solutions after the application is deployed. In a world where cybercrime is evolving at the same pace as technology, security practices need to be embedded into the application delivery workflow.
Security observability becomes a way for development teams to build applications that prioritize security from the initial stages, empowering teams to deal with potential threats throughout the development lifecycle. This new approach towards security has been termed the shift left paradigm, describing the process of addressing vulnerabilities from the very beginning of a development project.
Best practices for observability-driven security
To successfully combine observability and security, teams need to follow a set of best practices. This allows them to create ecosystems that are secure by default, starting from how developers configure their environments.
One of the most significant challenges developers face is setting up and managing the numerous technologies required for the software development lifecycle, including observability tools.
Putting in place a set of practices to secure data in the early stages is crucial. These might include:
-
Templates for secure configuration
-
Non-root mode
-
IP-based and other types of restrictions
-
Automatic signature verification
-
Automatic authentication of the environment
By safeguarding the infrastructure from the ground up, teams can create a robust environment for the application to thrive. Infrastructure as Code (IaC) Security is an important aspect of this, allowing engineers to identify misconfigurations and vulnerable default settings.
Another best practice involves integrating security with CI/CD pipelines and observability pipelines, which we`ll discuss in the following sections.
Integrating security into CI/CD Pipelines
Traditionally, continuous integration/continuous deployment (CI/CD) pipelines don`t address security concerns, forcing development teams to manage security as a separate process. By integrating automated security testing into CI/CD pipelines, teams can close this gap and ensure checks are performed at every stage of development.
This approach, also called DevSecOps, guarantees that vulnerabilities are detected and addressed before they reach production environments, allowing engineers to deal with issues as the application is built.
CI/CD pipelines automate the software delivery process, however, this automation should not come at the cost of security. With each code change, the potential for vulnerabilities increases. By embedding security assessments within CI/CD pipelines, teams can employ an additional layer of safeguards.
Scanning and analyzing source code
Static Application Security Testing (SAST) tools can be seamlessly integrated into the pipeline, offering real-time feedback to developers as they write code. SAST, also known as “white box testing”, helps identify issues early in development - in fact, it doesn`t even require the code to be executed, hence the word “static”. This allows engineers to fix issues without breaking builds or passing on vulnerabilities to the next development phase.
Assessing the security of third-party dependencies
Third-party dependencies and libraries can significantly speed up development, but they also introduce a potential Achilles' heel. Many high-profile breaches have exploited vulnerabilities in third-party dependencies.
To counter this, Source Composition Analysis (SCA) automatically assesses the security of open-source software in a codebase, including third-party libraries. This ensures that the final product is devoid of known risks or vulnerabilities, allowing teams to increase productivity without compromising quality or security.
Automating security testing and vulnerability remediation
Automated testing doesn't stop at functional and performance assessments—it extends to security testing. Automated security tests can simulate real-world attacks, such as SQL injection and cross-site scripting.
By running security tests alongside other performance checks in the CI/CD pipeline, development teams can gain better insight into their application`s state and security levels.
Additionally, the pipeline should be equipped with mechanisms to automatically remediate vulnerabilities when identified.
Runtime security and observability pipelines
Security monitoring and testing also need to continue after the application is deployed. Observability pipelines and tools allow security engineers to collect, process, and use data for threat detection and mitigation.
One of the most pressing challenges faced by security engineers today is the amount and diversity of data they need to keep track of, coming from multiple application components and environments. Observability pipelines reduce the amount of management work engineers have to do, allowing them better control over runtime application data and enforcing better security practices.
Observability pipelines explained
Observability pipelines enable teams to collect logs, metrics, traces, and other types of observability data from various sources, including AWS and Kubernetes containers, and send them to various destinations.
This approach comes with several significant benefits:
-
By centralizing everything into a single location, observability pipelines reduce the effort needed to manage telemetry data and detect anomalies.
-
Pipelines break down organizational data silos, making it easier for teams to exchange information and keep data consistent across different sources and formats.
-
Observability tools leverage pipelines and data visualization to create intuitive dashboards, graphs, and charts, allowing stakeholders across the organization better insight into system behavior and performance.
-
Pipeline real-time monitoring provides a comprehensive view of the application on multiple levels: resource utilization and performance, infrastructure insights, and scaling insights.

Leveraging observability pipelines for enhanced security
Primarily used for capturing performance data, observability pipelines can be extended to capture security-relevant information. By integrating security telemetry into these pipelines, organizations gain real-time insights into potential security vulnerabilities, unauthorized access attempts, and anomalous behaviors.
Here are some of the ways observability pipelines support enhanced security efforts.
Early anomaly detection
Traditional security practices used to focus on investigation incidents after the fact. Observability pipelines flip this narrative by allowing early detection of anomalous behavior such as sudden spikes in network activity or strange authentication behavior.
Machine learning algorithms used by observability pipelines can analyze incoming data streams and identify patterns that deviate from the norm in a proactive manner.
Real-time incident response
By using continuous monitoring and alerts, observability pipelines enable security teams to take action almost instantly, minimizing the impact of security incidents. When a potential breach is detected, the pipelines trigger previously set alerts, notifying administrators.
Depending on how the alerts are configured, they can also automatically fix issues without human intervention, speeding up the response time even more.
360-degree view of security incidents
Observability pipelines provide a comprehensive view of security incidents, not only in terms of correlating data but also in terms of predicting future threats and learning from past events.
Security teams can leverage observability to understand how an incident unfolded, trace its origin, and assess its impact, as well as prevent it from happening again.
Compliance with security regulations
Security observability pipelines play a crucial role in maintaining compliance and facilitating auditing processes. By capturing and analyzing security-related data, these pipelines ensure that regulatory requirements are met.
In the event of an audit, the historical data stored in observability pipelines can be invaluable in demonstrating compliance.
Conclusion
In an ever-evolving threat landscape, development, and security teams are faced with constant challenges. Securing modern applications against attacks requires a more proactive and dynamic approach than traditional monitoring affords.
Integrating observability-driven development and security emerges as a powerful strategy to overcome these challenges and make security a priority throughout the entire development lifecycle.
By combining observability and security, teams can gain better insight into security incidents, act on them faster, and overall build more resilient applications.